What is a machine connector?
A machine connector is a plugin that acts as a middleware to communicate between the Venafi Platform to any 3rd party applications. The connector is responsible for authenticating, pushing, and configuring the certificate from Venafi to any application of the client’s choice. In the Venafi world, every connector is a REST-based web service with certain predefined APIs implemented to perform a task. Venafi provides a connector framework to help build more connectors easily to support the clients’ ecosystem.What is a machine connector framework?
The Venafi machine connector framework provides the following:- Step-by-step guidance
- An easy to use template
- A faster way to build and test a TLS Protect Cloud connector
To work effectively with any Venafi connector framework, you must have some working knowledge of the Go Programming language.
How do I get started?
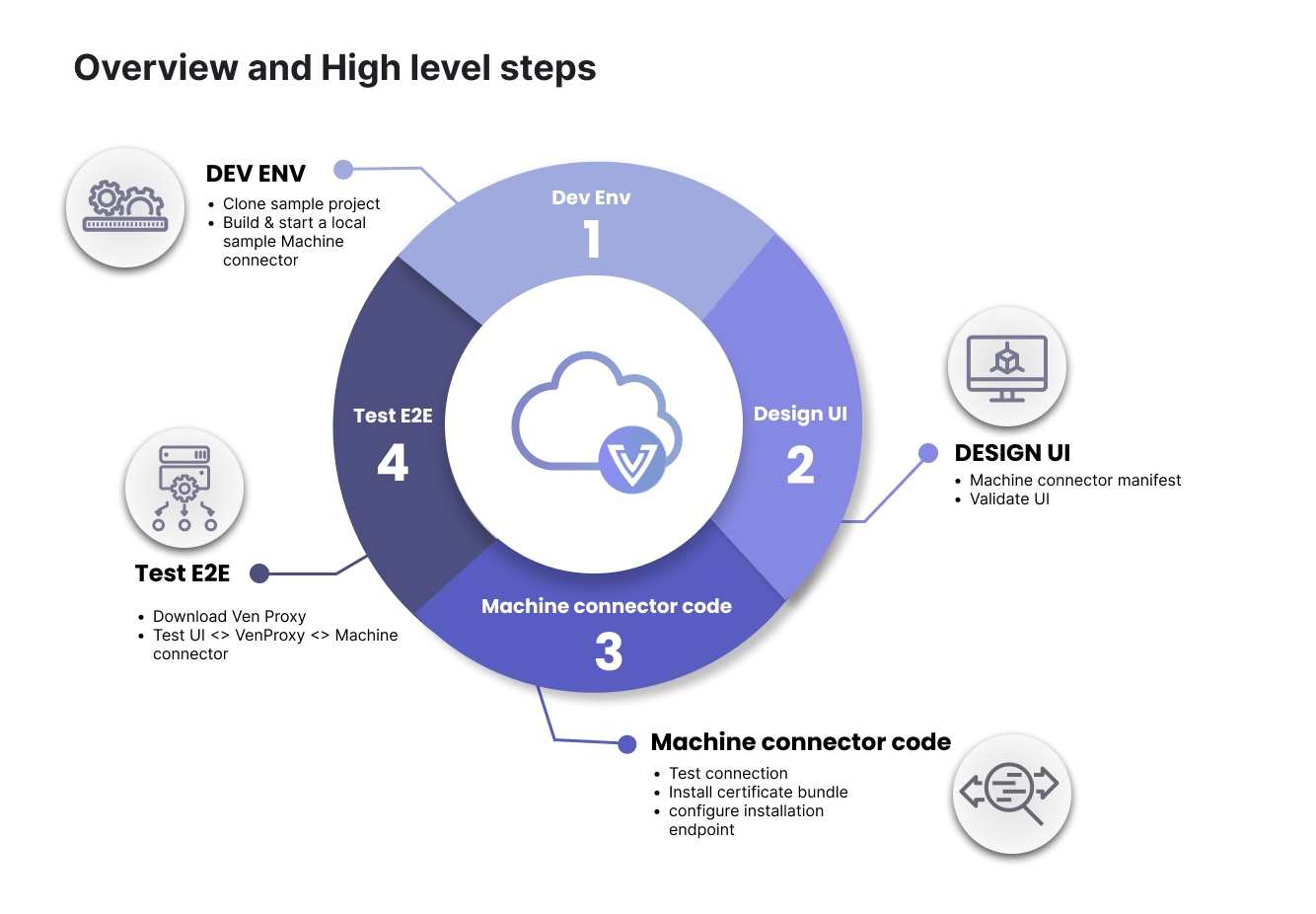
-
Set up your developer environment. You have to options in this step, choose the one that fits your needs.
-
Sample push connector - Download and unzip the
sample-push-connectortemplate. Here, we will walk you through building and running a local sample connector. - VMware AVI OpenSource - Clone our VMware AVI OpenSource connector. This option makes creating the manifest and the code much easier because this is a working pre-built, ready-to-go alternative that contains a manifest, source code, and makefile to create an image. The OpenSource connector provides developers with all the necessary components to construct a Docker image, ready for uploading to a container registry. From that point, developers can update the manifest to incorporate the container registry path and use it in TLSPC production. Note that you will need a registry for this option.
-
Sample push connector - Download and unzip the
- Design the UI (front-end). We will provide you with a default manifest editor. This environment allows you to develop and validate your data. We also provide you with a manifest reference, which allows you to customize your manifest to fit your needs.
-
Build connector code (back-end). Create the web-service back-end connector code using the files from the sample-push-connector template. The two files you will use are:
- main.go - this file contains a declaration of the 3 APIs we will use.
- handlers.go - this file contains the functions which implement these APIs. This is where we will define all the logic (e.g., how we connect to the server, how to install the certificate bundle, etc.).
- Test E2E. Test end to end via the manifest editor and the VenProxy simulation utility. The VenProxy simulation utility creates the bridge from the simulation environment to your locally connected developer environment. This is where we will validate that your front-end UI on the manifest editor is connected via the VenProxy simulator to your back-end connector code.
Step 1: Set up your developer environment
Again, you have two options for this step. Use the sample-push-connector template, which is more of a manual hands-on approach to building your connector, or use the VMware AVI OpenSource pre-built, ready-to-go connector, saving significant time.Sample push connector option
For this walk-thru, we will provide you with a sample-push-connector template that you can use to add more logic and customize it to fit your environment.- Download and unzip the sample-push-connector template. Compile the sample-push-connector template.
- Change the working directory to where the sample-push-connector is located.
-
Run the buildcommand and then run the sample-push-connector. That should start your connector on port 8080.
VMware AVI OpenSource option
If you choose to use our VMware AVI OpenSource connector, you will need to set up a container registry. A container registry is a repository or collection of repositories, used to store and access container images. Container registries can connect directly to container orchestration platforms such as Docker and Kubernetes.Container repository - storage for your containerized application images.Container registry - acts as both a collection of container repositories and a searchable catalogue where you manage and deploy images.
Dependencies
You will need the below dependencies to use this option:- GNU Make 3.81
- jq - commandline JSON processor [version 1.6]
- go version go1.20
- Docker version 24.0.7
- golangci-lint has version 1.52.2
Setting up environment variables
To build an image that will be run within a Venafi Satellite for provision and/or discovery operations you will need to define a CONTAINER_REGISTRY environment variable.Step 2: Design the UI (front-end)
You will create the front-end UI using the manifest editor. As you build out your manifest, you can validate your data. See the below example:You will notice a “Login” button in the top right-hand corner. At this point, you do not need to login to start creating your manifest. Instead, you can begin to create your manifest, reset it if necessary, and edit it until you are happy with it. However, you must log in with your Venafi credentials when you are ready for end-to-end testing in step four.
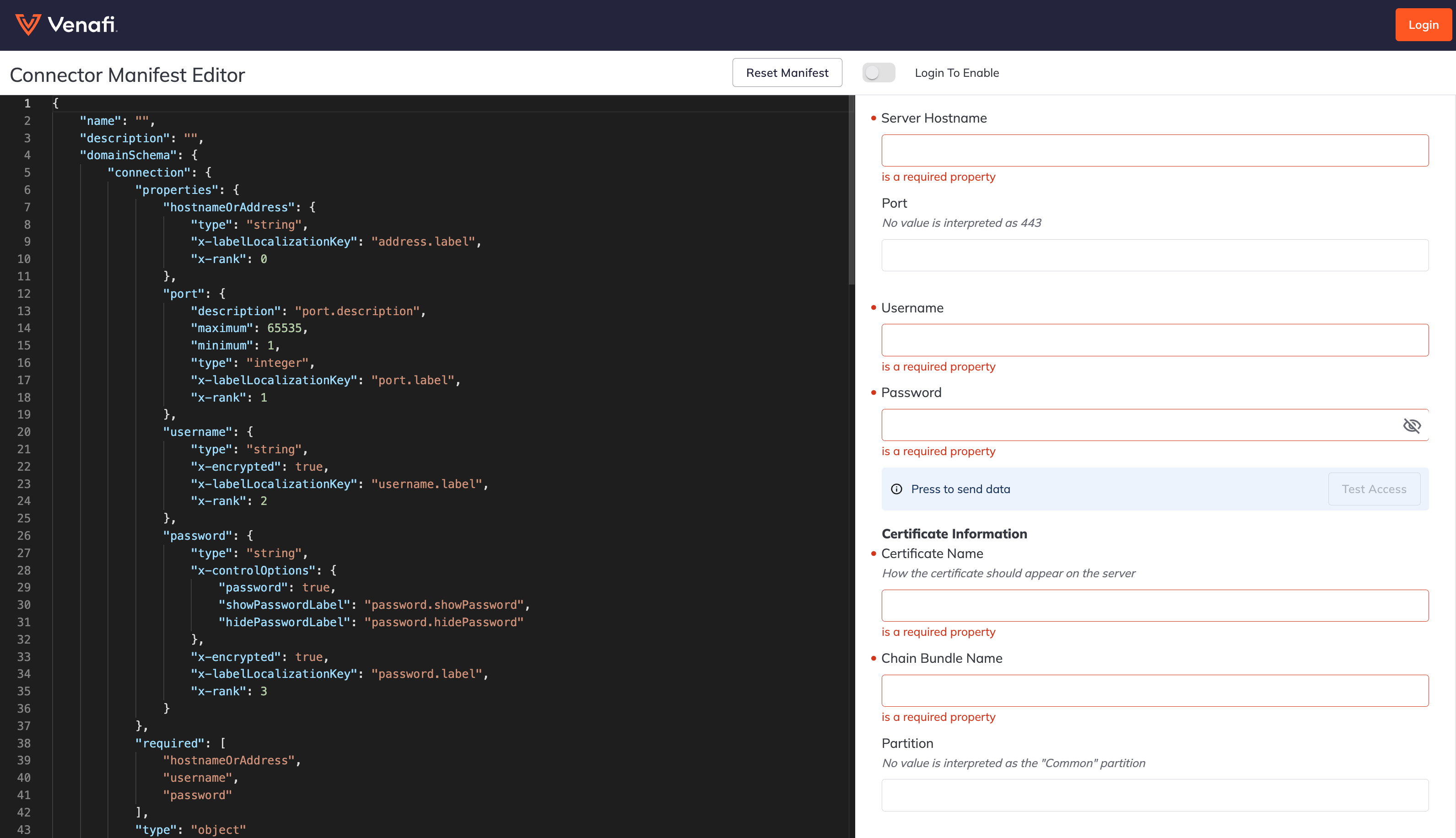
- Build out your manifest using the JSON form. This manifest will dictate how your front-end UI will look. Use the left pane to change anything needed for your specific environment, and the results will be dynamically populated in the right pane of the editor. You can use the manifest reference to customize the UI based on your specific needs.
Step 3: Build connector code (back-end)
- Create your web-service back-end connector code using the files from the
sample-push-connectortemplate. There you will find two files (main.go and handlers.go).
APIs
/v1/testconnection- This API takes the connection details and responds back with a success or failure connection to the system we are building a connection for./v1/installcertificatebundle- This API takes the certificate bundle, connection details, and target information (key store) on where the certificate bundle needs to be installed. A handler must be defined to provide business logic on how to install a certificate bundle to the external system./v1/configureinstallationendpoint- This API takes the connection details, endpoint details, and the JSON returned frominstallcertificatebundleand configures it. If the install command returns a 200 and a body such as{"mydetail":{"installed_certificate_id":23546324}}then the JSON sent toconfigureinstallationendpointwill contain the VaaS supplied data from the UI for “connection” and “binding” (e.g., endpoint fields from the UI) as well as “mydetail”. In this example you would see{"connection"{...},"binding":{...},"mydetail":{"installed_certificate_id":23546324}}./v1/discovercertificates- This API is recommended and indicates that your connector supports certificate discovery.

